connect.ngrok-agent.com:443. You can change this per agent by setting the
connect_url field in your configuration file.
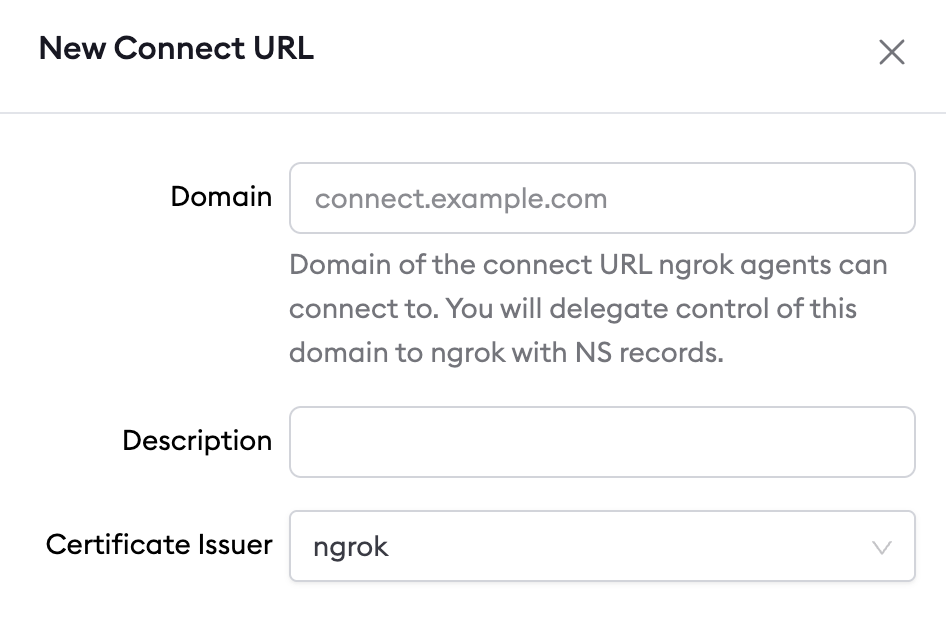
Custom connect URL
Create a custom Connect URL to customize how your agents connect (for exampleconnect.example.com:443). This involves delegating a DNS subdomain and
configuring certificates for the new address.
Key points:
- Agents connecting via your custom Connect URL must authenticate to your ngrok account; connections using credentials from other accounts are rejected.
- Custom Connect URLs support both ngrok‑issued and Let’s Encrypt certificates.
Create a custom connect URL
- Choose a domain you own
- You will delegate a subdomain via
NSrecords to ngrok so it can manage the required DNS (A/AAAA) and certificates.
- Create the Connect URL entry
- In the Dashboard: https://dashboard.ngrok.com/ingress
- Or via API: /api-reference/agentingresses/list/
- Pick a certificate issuer
- ngrok Internal CA (fast, private CA, may require trust in some networks)
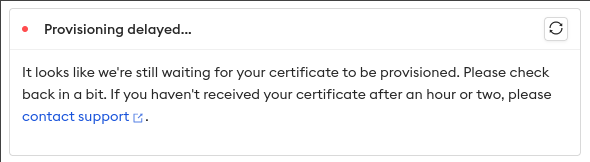
- Let’s Encrypt (public CA, may require additional provisioning time)
Delegate DNS records
After creation, the Dashboard prompts you to addNS records for the selected
subdomain at your DNS provider.
Update Agent configuration
Point your agents at the new address by settingconnect_url. The helper command
ngrok config add-connect-url can
update your config for you.
For example, if the domain of your custom Connect URL is
connect.example.com then you might add the following line to the agent’s
configuration file:
- Agent CLI
- Agent Config
- SSH Reverse Tunnel
- Go
- Javascript
- Python
- Rust
- Kubernetes Controller
Regional scope and GSLB
Custom Connect URLs are pinned to a specific region for the agent’s control connection and do not use Global Server Load Balancing for that connection. End-user traffic to your endpoints is still delivered using GSLB.Dedicated IPs
When you create a custom Connect URL, the DNS and certificates are branded to your domain, but the address still resolves to ngrok’s shared IPs. If you need static, account-unique addresses, dedicated IPs are available. Contact Sales for details.Certificate issuer
When you create a custom Connect URL, choose one of two certificate issuers:- ngrok’s internal CA
- Let’s Encrypt
ngrok internal CA
- Default option; provisioned immediately.
- Trusted by the ngrok agent out of the box.
- Some enterprise inspection tools may not trust this private CA without additional configuration.
Let’s Encrypt
- Public CA; useful when corporate proxies or network devices cannot trust a private CA.
- May require setting
root_cas: host(or providing the Let’s Encrypt root) for some SDKs and for the SSH Reverse Tunnel agent. - Provisioning can take time (DNS propagation). ngrok issues a temporary certificate until Let’s Encrypt is ready. Even if DNS checks pass in the Dashboard, Let’s Encrypt may still be propagating.
Certificates issued by Let’s Encrypt through ngrok are securely managed.
Private keys are not exposed to requesters.
Why customize the connect URL?
Branded connectivity
If you use ngrok for production connectivity (devices in the field or customer environments), a custom Connect URL lets you brand connectivity with your domain.Policy enforcement
For development and testing, a custom Connect URL helps enforce policy:- Ensure developers use a shared ngrok account (not personal accounts).
- Block default Connect URLs on corp networks while allowing your custom URL.