AWS Kinesis Event Destination
To send ngrok events to Kinesis:
This guide covers how to send ngrok events including network traffic logs into AWS Kinesis. You may want to keep an audit log of configuration changes within your ngrok account, record all traffic to your endpoints for active monitoring/troubleshooting, or you may use AWS Kinesis as a SIEM and want to use it for security inspections.
By integrating ngrok with Kinesis, you can:
- Quickly identify application issues in real-time using ngrok request events using Kinesis data processing.
- Historically audit changes occurring within an account. Be able to historically audit changes within an account.
- Profile usage of your service by using Kinesis queries and real-time data analytics.
- Identify security issues by using ngrok events.
Step 1: Obtain Kinesis Data Stream ARN
For ngrok to successfully send events into Kinesis we'll require a data stream ARN. To create the AWS Kinesis Data Stream and retrieve the ARN, reference the AWS documentation for Creating a Kinesis Data Stream.
Step 2: Create an Event Subscription
-
Using a browser, go to the ngrok dashboard and navigate to Events on the left hand navigation and select Create Subscription.

-
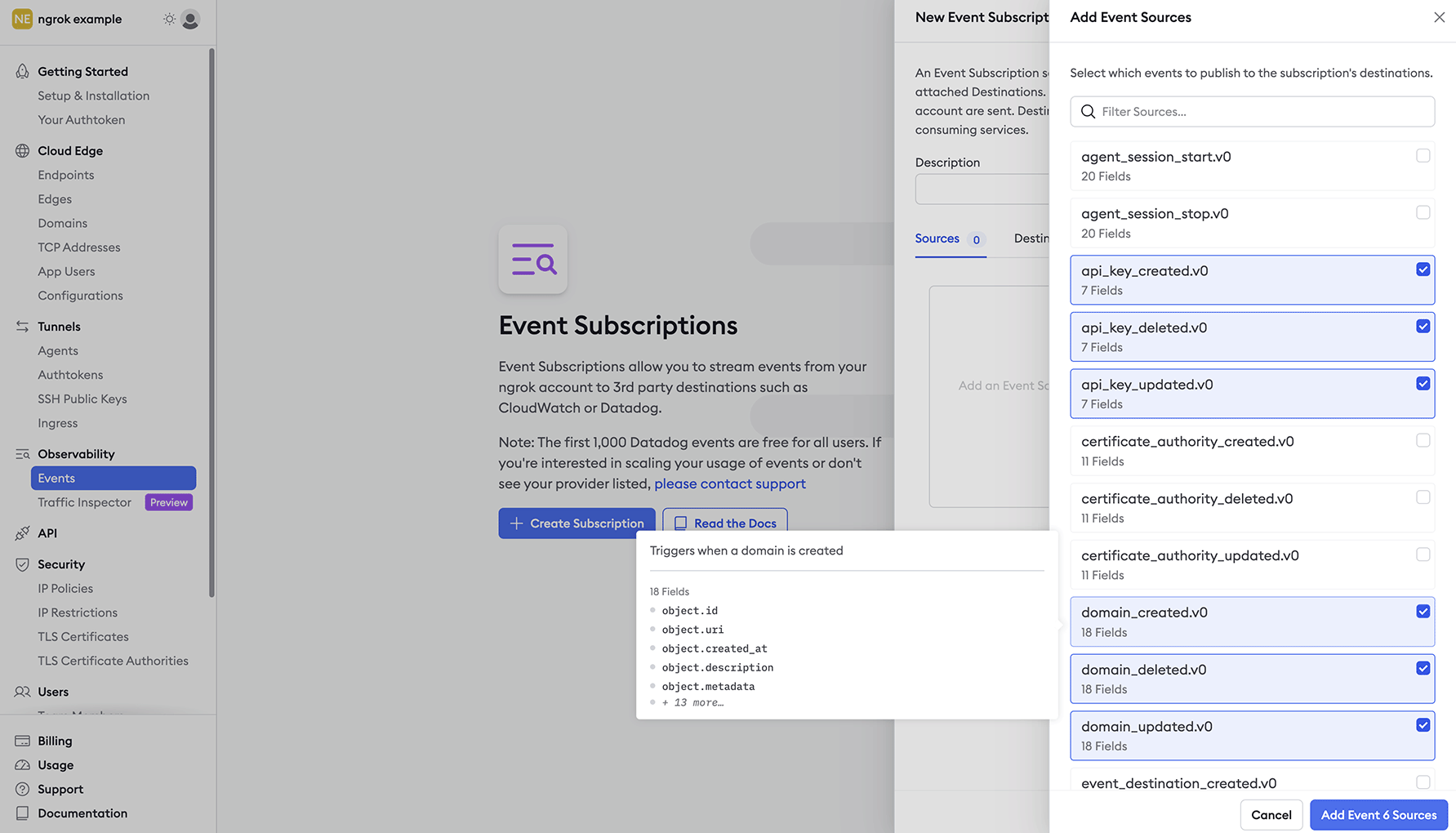
Within the Event Subscription configuration, provide a description for the event and within the sources tab select Add Source to pick and choose which events you would like to send to Kinesis.
Once complete, select Add Event Sources to confirm your selections.
Step 3: Create Event Destination
To send the events to Kinesis we'll need to assign an Event Destination to the Event Subscription.
-
Within the Event Subscription configuration Destination Tab, select Add Destination.
-
Choose AWS Kinesis as the target and fill in the correct information.
- Stream ARN
- Description - Optional
-
Create IAM Role - An IAM role is required to allow ngrok to stream logs into Kinesis. Using the information provided by your preferred method of creation, either API or CLI Script, create the IAM role and provide the role ARN. For the fastest integration or proof of concept, we recommend using the CLI Script.
If configuring your IAM role manually, ensure that you configure the Trust Policy with a condition that includes the ExternalId. This will ensure that the only data allowed to ingested by AWS will be from your ngrok account. If you configure the IAM role with the CLI script, this will be done automatically.
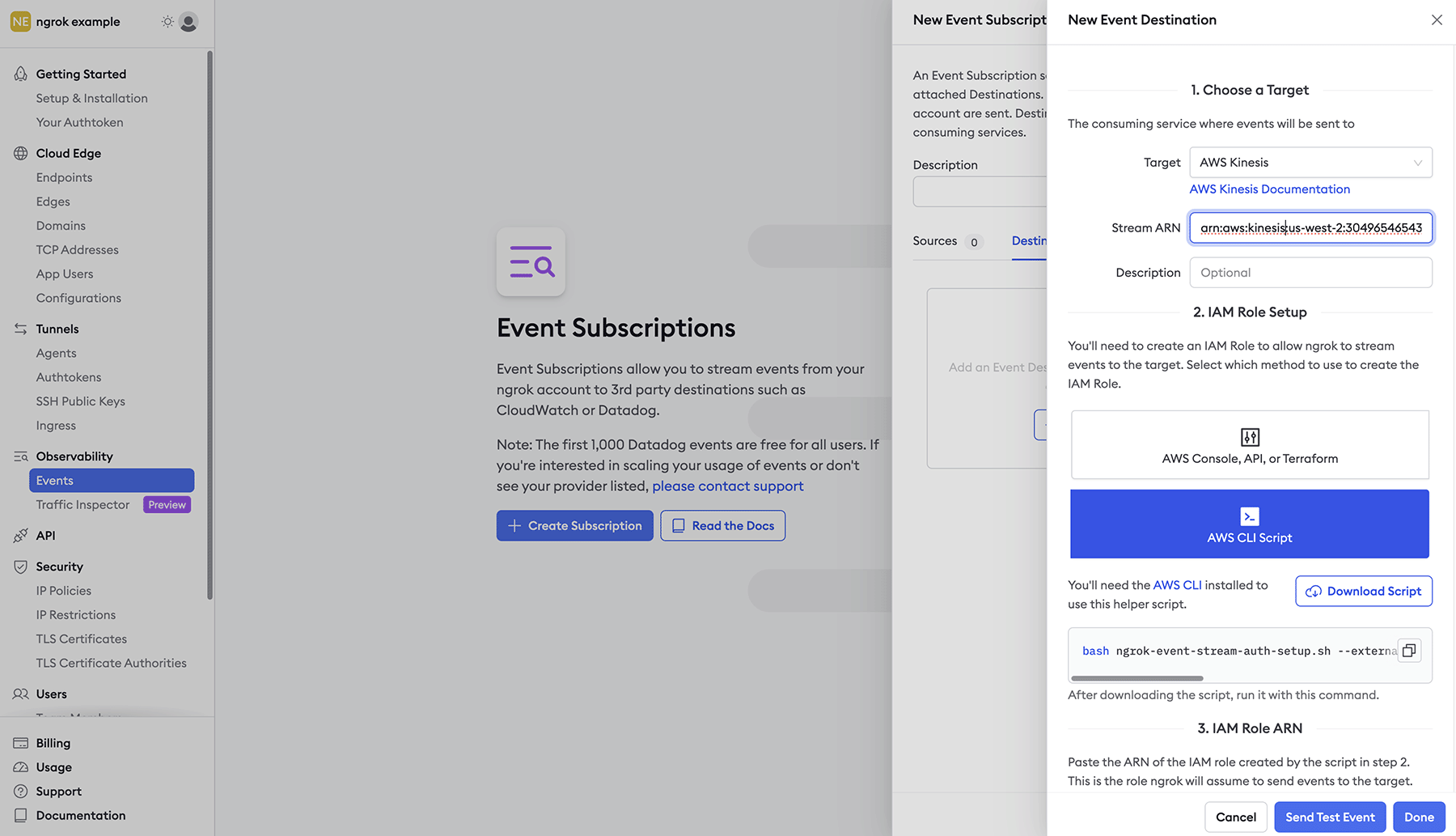
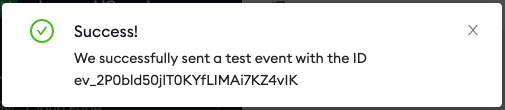
- Once all required inputs have values, select Send Test Event and you should be presented with a Success message. Select Done and the Kinesis Event Destination setup is complete.