terminate-tls Traffic Policy action.
What you’ll need
- Ensure you have openssl installed.
1. Provision your certificates and credentials
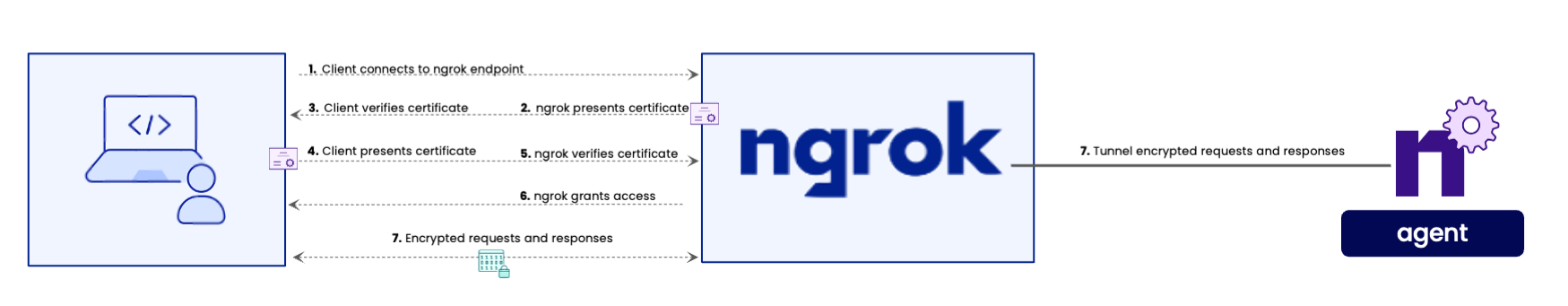
Although ngrok can automatically provision your certificates when you use standard TLS, you’ll have to provide your own TLS certificate authority (CA) for mTLS. The CA is responsible for issuing, digitally signing, and verifying the authenticity of client certificates. Keep in mind:- ngrok uses the CA certificate to verify the client certificate.
- Once the CA signs a client certificate, the client certificate is used to grant the client access your endpoints.
- ngrok does not generate CA and client certificates for you when you use mTLS; you must generate them yourself.
- Though your CA certificate must be uploaded and hosted on the ngrok SaaS platform, your client certificates need to be distributed to any client or device that needs access to your endpoints.
Generate your own certificates
Most organizations have their own certificate management infrastructure, so this step is optional if you already have a CA and client certificates to work with.
ca.key, ca.crt, client.key, client.csr, and client.key.
You will use the contents of ca.crt in your Traffic Policy to validate requests via curl, which, in turn, uses client.key and client.crt.
2. Create a Traffic Policy
Using the CA certificate generated in the previous step, you can specify themutual_tls_certificate_authorities field in a Traffic Policy to trust the CA that issued the client certificate.
mutual_tls_certificate_authorities array.
3. Start an endpoint with the Traffic Policy
4. Test your endpoint
Test out that everything works by making a request to your endpoint using the--cert and --key flags to specify the client certificate and private key.