Prerequisites
To use the sample application, you need the following prerequisites on the device or device gateway you wish to connect to:- Python 3.11
- venv or another Python virtual environment manager
Get an ngrok API key
Create an ngrok API key using the ngrok dashboard. Make sure you save the API key before you leave the screen because it won’t be displayed again.Reserve a domain for wildcard endpoints
Reserve a wildcard domain, which will allow you to create wildcard endpoints and receive traffic on any subdomain of your domain. For billing information, see wildcard endpoints pricing. For example, you might create*.sitea.{YOUR_DOMAIN}. You would then be able to create endpoints
on device342.sitea.{YOUR_DOMAIN} and device896.sitea.{YOUR_DOMAIN} without having to reserve them individually.
It can be helpful to create a separate subdomain for each site you wish to connect to.
Run the following command, substituting your API key for {API_KEY} and your domain for {YOUR_DOMAIN}:
201 response similar to the following:
Update DNS records
Next, add twoCNAME records to your DNS provider’s registry, providing values from the previous response.
Add a CNAME record for the domain you just reserved.
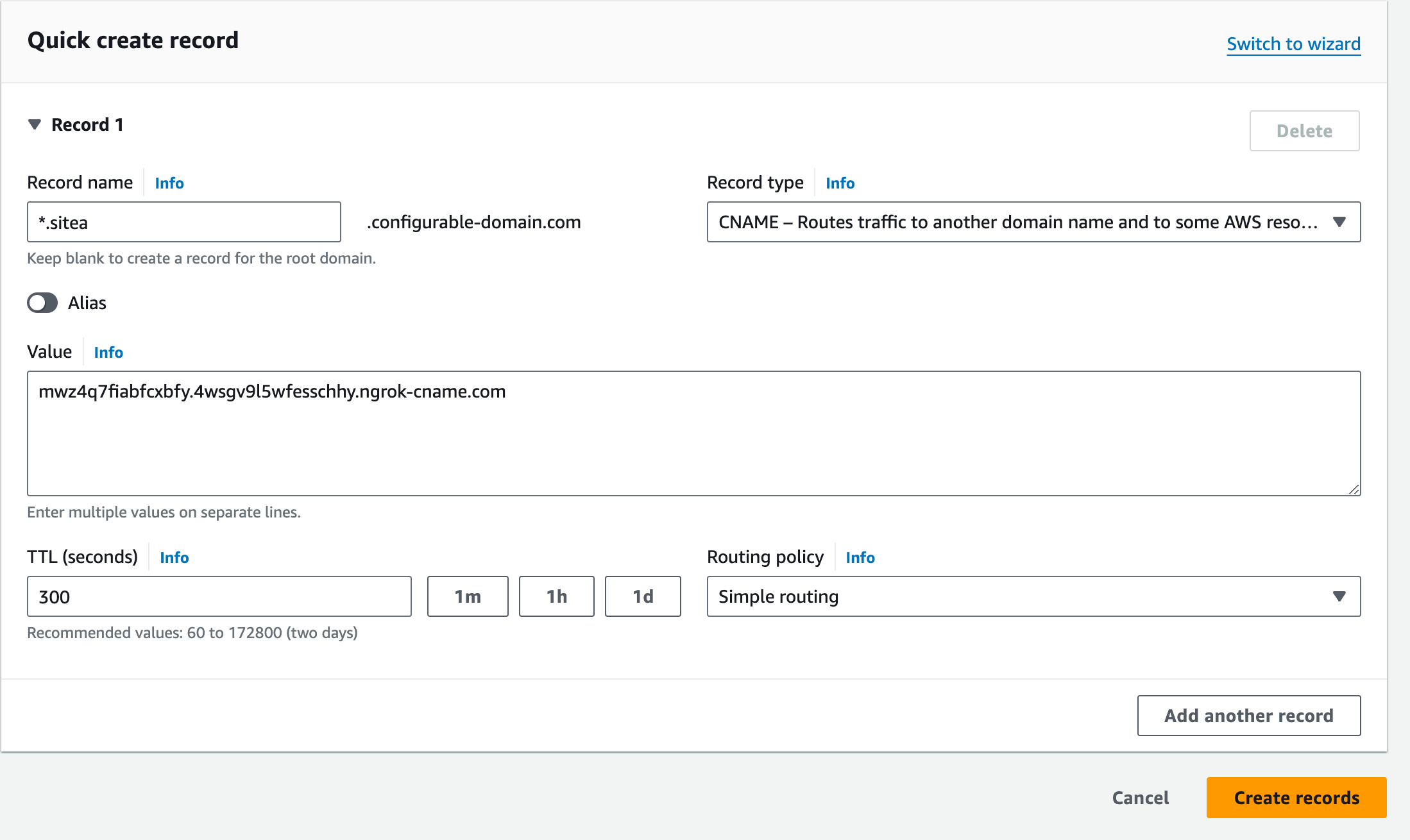
_acme-challenge.{SUBDOMAIN}, and use the value of the acme_challenge_cname_target property from previous response for the value. For the example above, the record name would be
_acme-challenge.sitea.
Verify DNS
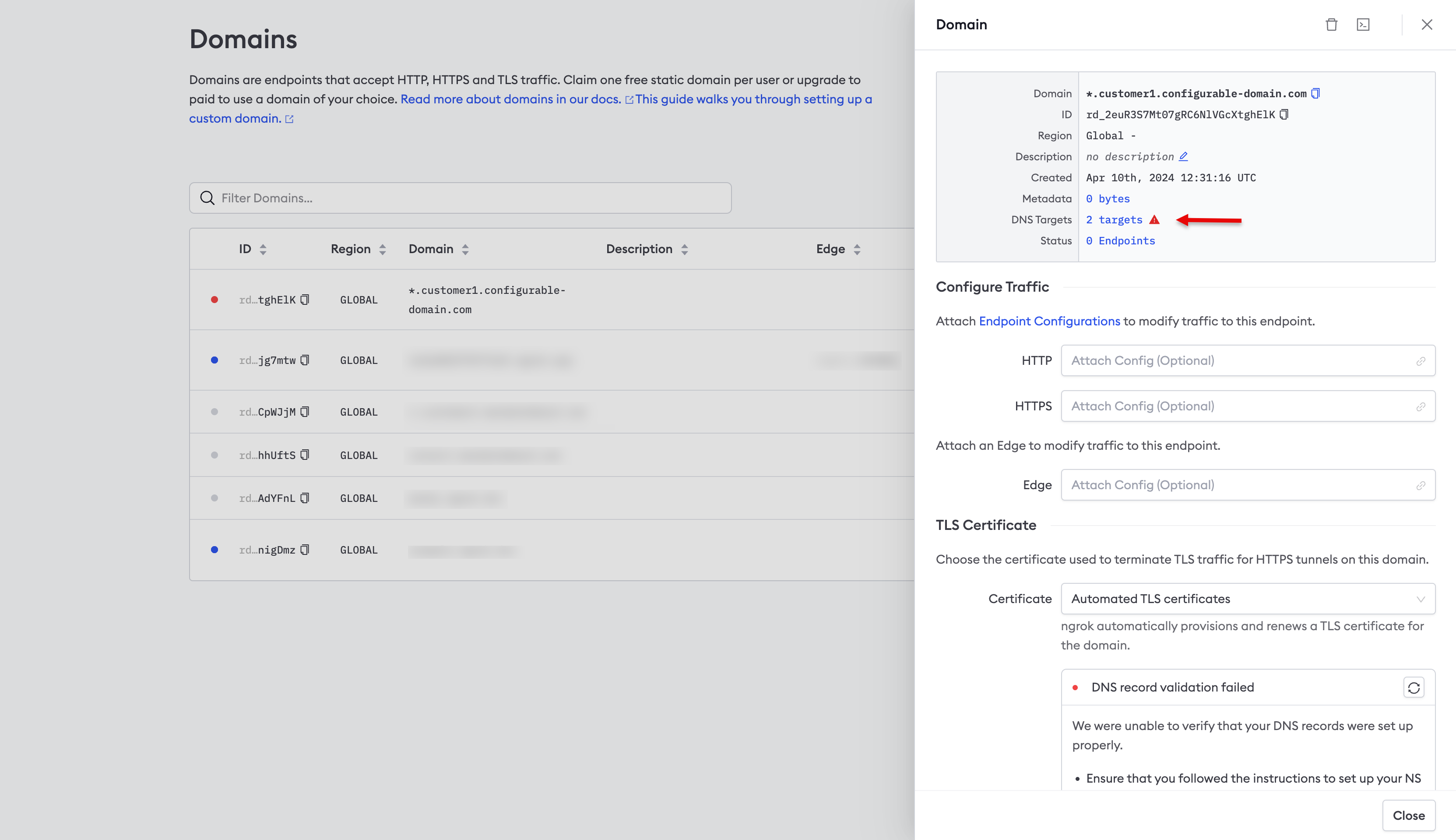
Use the ngrok dashboard to verify that you’ve configured DNS correctly.- Login to the ngrok dashboard.
- Click Domains in the left-hand navigation menu.
- Click on your domain under Domain.
- Click 2 targets next to DNS Targets in the panel displayed on the right-hand side of the screen, as denoted by the arrow in the screenshot below.
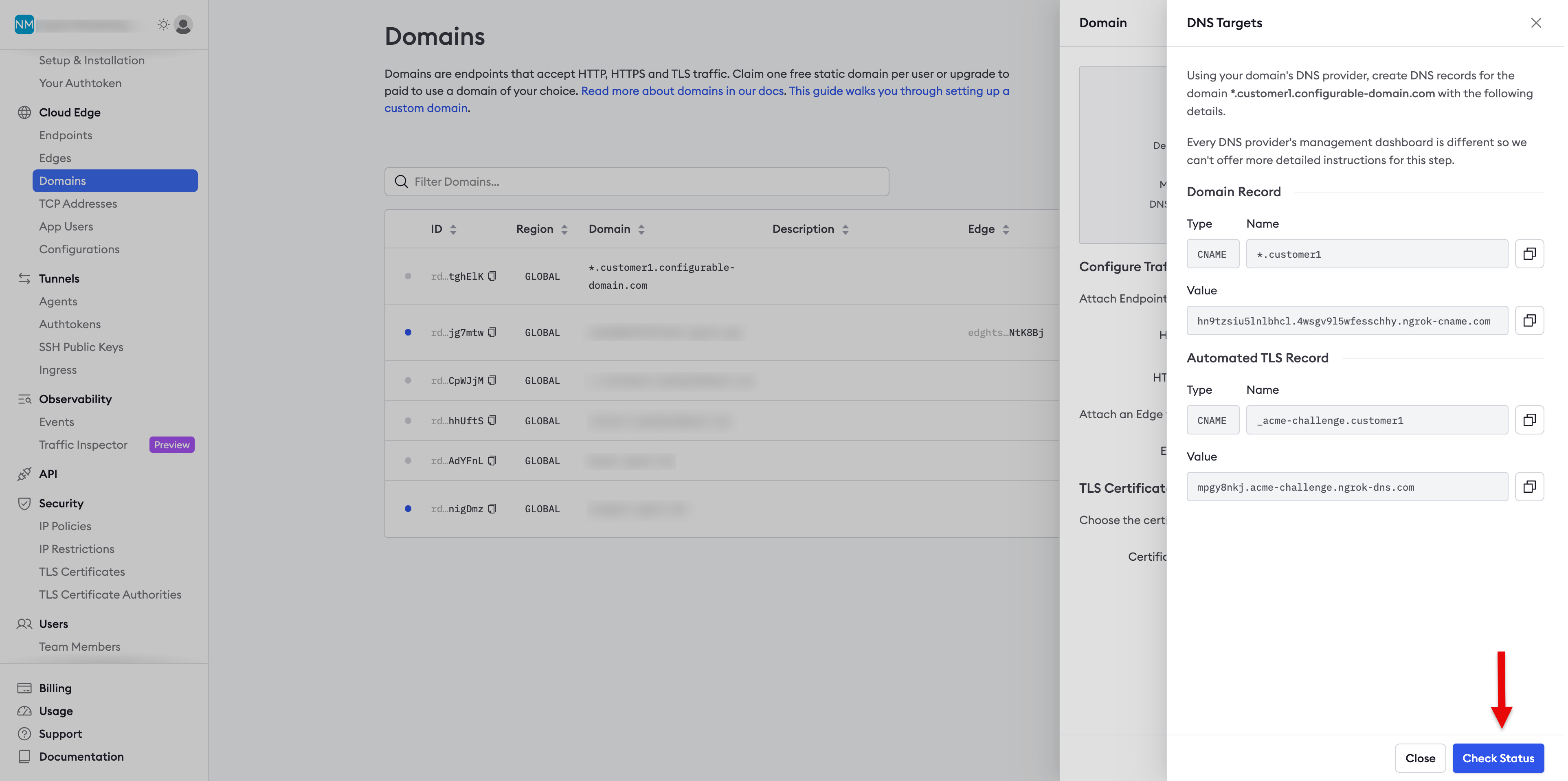
- Click Check Status, as denoted by the arrow in the screenshot below.
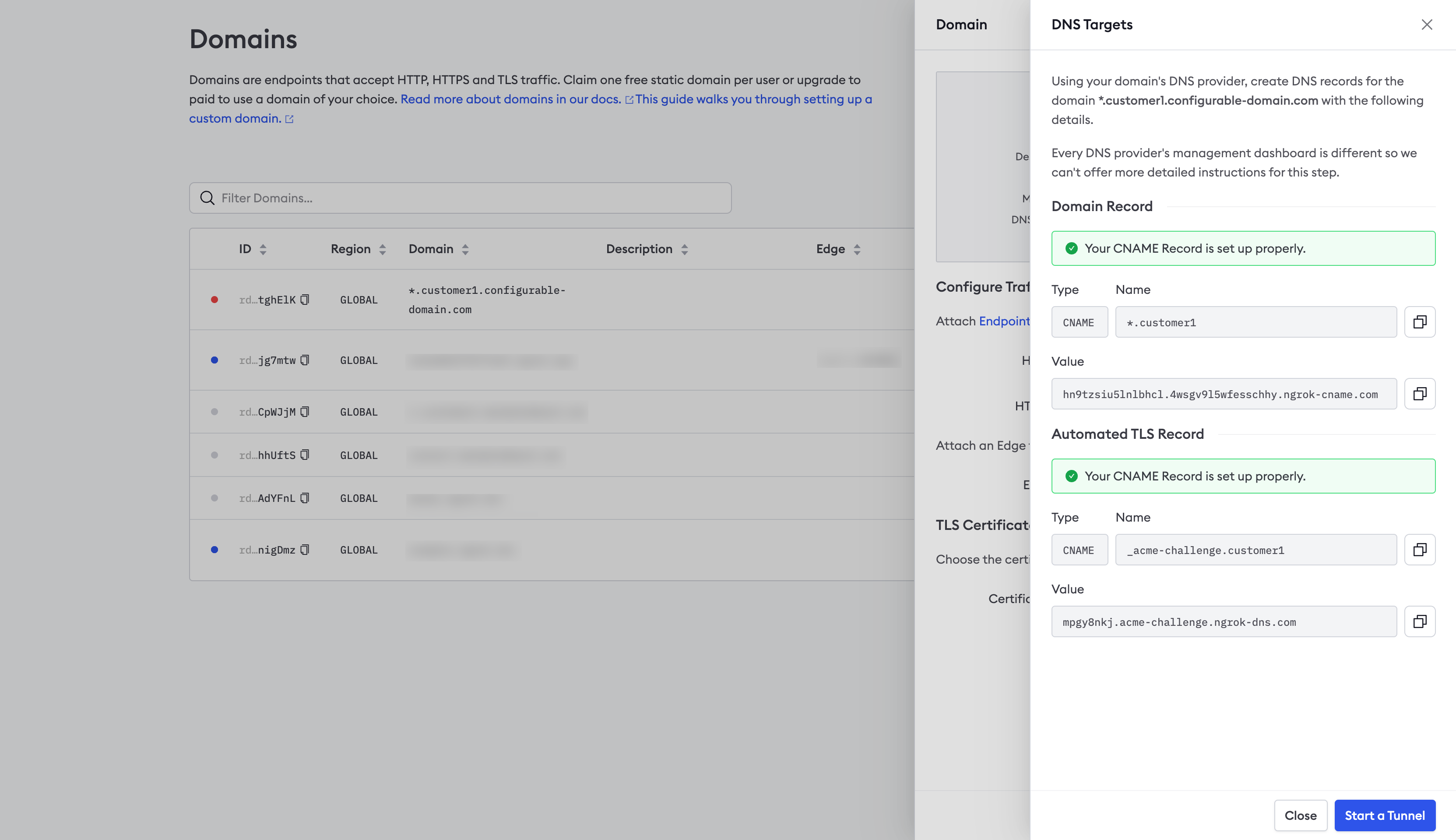
- You should see a successful response similar to the screenshot below.
Create a Service User
You’ll create a Service User so that in the next section, you can create an agent authtoken independent of any user account. A Service User does not belong to a particular user account. Run the following command to create a new Service User, providing your API key and a description:201 response similar to the following:
Create the Agent authtoken
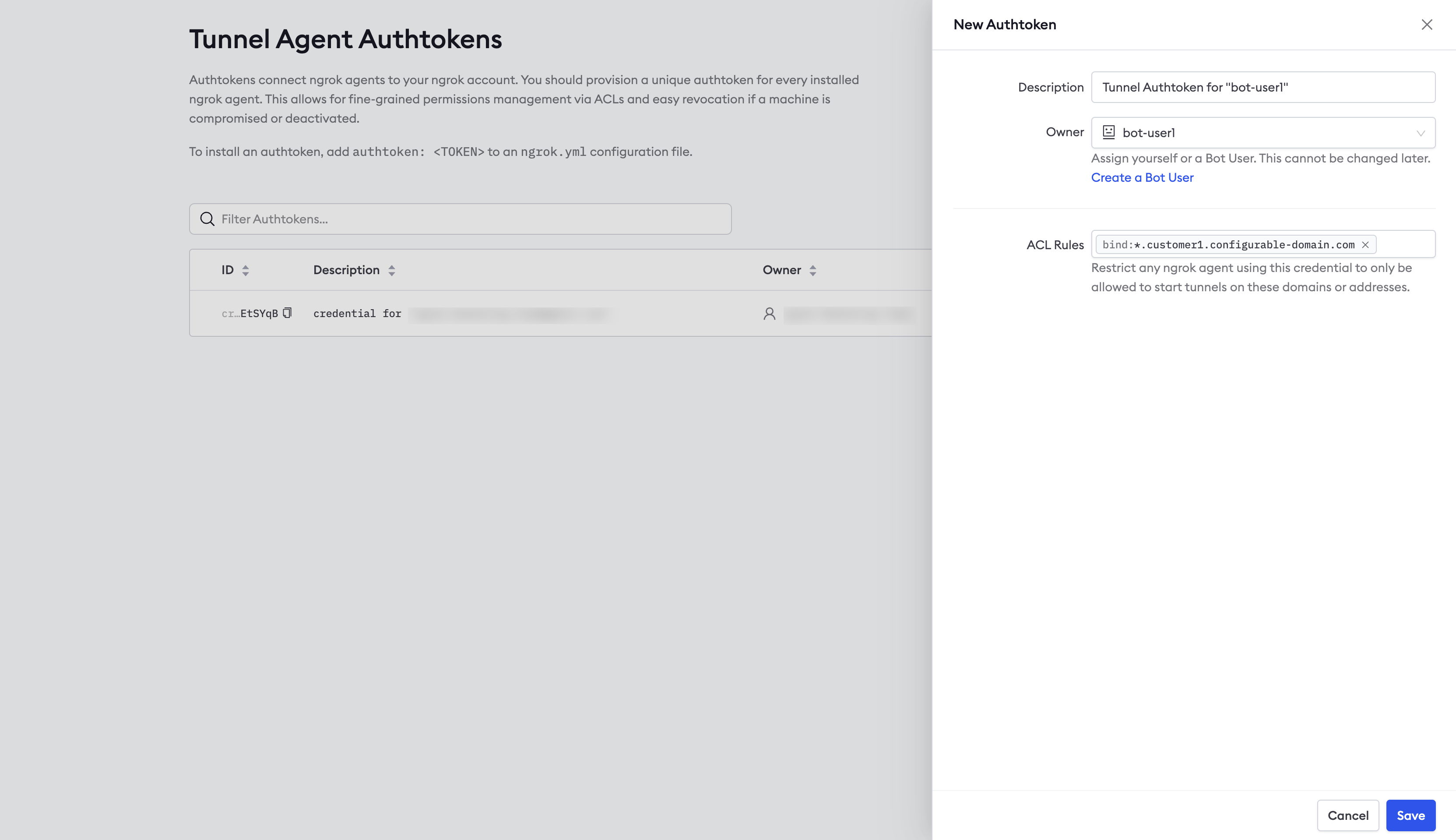
You should start each agent using a separate authtoken, and that token should belong to a Service User. To create an authtoken, login to the ngrok dashboard and click Authtokens under Tunnels, then click Add a Tunnel Authtoken. For Owner, select the Service User you use created, and selectbind:*.sitea.{YOUR_DOMAIN} for the ACL Rules.
This ACL will allow an agent with the authtoken to create tunnels on any subdomain of sitea.{YOUR_DOMAIN}.
Configure the sample Agent
The sample application uses the ngrok Python SDK to embed connectivity directly into the application rather than using the standalone ngrok agent, the CLI, or the ngrok Kubernetes Operator. It serves a local REST API you can use to create, delete, and list tunnels.Clone the repo
Clone the ngrok-samples/ngrok-python-iot-agent repo on the device or device gateway you wish to connect to.Create and activate a virtual environment
Run the following to create a virtual environment, providing a directory for{PATH_TO_VENV}:
python -m venv {PATH_TO_VENV}
Run the appropriate command for your O/S to activate the virtual environment:
- In cmd.exe:
{PATH_TO_VENV}\Scripts\activate.bat - In PowerShell:
{PATH_TO_VENV}\Scripts\Activate.ps1 - Linux and macOS:
source {PATH_TO_VENV}/bin/activate
Install dependencies
Runpip install -r requirements to install the dependencies.
Update the domain
Update line109 with your domain. Since you reserved a wildcard domain, you can create endpoints on any subdomain
of that domain without reserving them individually. For example, for the domain *.sitea.configurable-domain.com, you could create an endpoint at api.sitea.configurable-domain.com.
Set your authtoken
This sample application is designed to read your ngrok credentials from the environment, so run the following command, replacing{YOUR_AUTHTOKEN} with the authtoken you created in the previous
step:
Use the sample app
This sample application is a custom ngrok agent built using the Python SDK. In a previous step, you updated the domain on line109 of agent.py.
This domain will be used to serve a local REST API built into the sample application using FastAPI.
You’ll use this API to create, delete, and list tunnels remotely.
The application persists tunnels in a local JSON file, ngrok_config.json, and recreates them when the application is restarted. You could extend this application to store tunnel configuration in a backend database.
You may pass policy information directly in the body of the request. The application includes a JSON
file, test.json, which contains the default policies it applies to any new request that doesn’t specify policy information. You could update this file to control policies applied to new tunnels rather than passing the policy information in each request.
Start the app
Run the following to start the agent:List tunnels
Run the following command to list tunnels started by this custom agent application, substituting the domain you set on line109 for {YOUR_AGENT_DOMAIN}:
200 response with an empty array.
Start a tunnel with default policies
Run the following command to start a tunnel to the device or device gateway where the custom agent application is running, substituting the appropriate values for the variables:{HOST}- the host where the API is running, leave blank and remove the colon forlocalhost{PORT}- the port where the API is running{TUNNEL_DOMAIN}- the domain you want to serve the API on the device or device gateway{YOUR_AGENT_DOMAIN}- the domain you set on line109of the code
200 response similar to the following:
policy property is null. This is because the request didn’t include
any policies. However, this sample application applies the default policies defined in test.json
if no policies are included in the request.
List tunnels
If you run the request to list tunnels again, you should receive a200 response similar to the following. Notice that it includes the policies defined in test.json. You can update the policies
in this file to the defaults you want applied to new tunnels when no policies are specified in
the request:
Start a tunnel with policies
Run the following command, substituting the appropriate values for the variables to create a new tunnel, specifying policies directly in the request.200 response similar to the following:
Delete tunnel
Run the following command to delete a tunnel, substituting{YOUR_AGENT_DOMAIN}
with the value you set on line 109 of the code and {URL_PART} with the value of the
url_part property of the list tunnels request:
Access the API running on the device or device gateway
You should now be able to access the API on the device or device gateway using the value from{TUNNEL_DOMAIN} in the request to remote manage your device fleet.